AlexOlesh
Member
- Messages
- 9
- Points
- 3
Hello all,
I have a very wierd situation.
NVR: DS-7604NI-K1(B), latest firmware v4.30
Connected to a TP Link router via Ethernet cable. ISP gives a dynamic IP address. Hik-Connect activated, however, the app is disabled.
The problem happens every time after somebody tries to make a remote login using the admin username. Immedately after that the following starts happening:
Host Name for 35.208.251.78
Host Name: 78.251.208.35.bc.googleusercontent.com
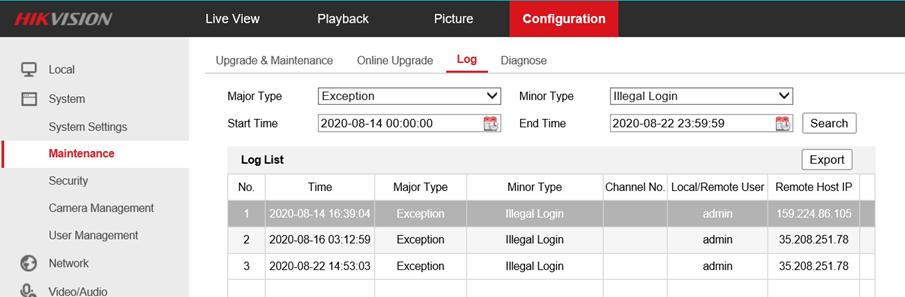
Any idea how can I block such illegal login attempts? Does it help to change the default ports on the NVR? If so, then which ones? Any other ideas on how to block 'em from accessing my NVR? Could I block some specific ports in the TP Link router firewall? It is getting really annoying that some mom's hacker is just scanning the network for NVR's to attempt to access. Any other ideas on securing the network are very warmly welcomed.
Thanks!
Alex
I have a very wierd situation.
NVR: DS-7604NI-K1(B), latest firmware v4.30
Connected to a TP Link router via Ethernet cable. ISP gives a dynamic IP address. Hik-Connect activated, however, the app is disabled.
The problem happens every time after somebody tries to make a remote login using the admin username. Immedately after that the following starts happening:
- the continuous recording stops
- the cameras, connected to the NVR, continue to register the motion detection alarms, that are visible in Logs
- the NVR becomes unavailable via iVMS-4500 on my Android phone
- The whole setup gets back to life only after button restart on the NVR.
The IP addr resolves to some googleusercontent.com hostCO CIE BOLI, ZE RYCHU PEJA MA SZANSE UCZCIWIE ZAROBIC?
(translation to English: WHAT DOES IT HURT YOU THAT SOON PEJA HAS A CHANCE TO EARN HIS FAIR SHARE?)
Host Name for 35.208.251.78
Host Name: 78.251.208.35.bc.googleusercontent.com
Any idea how can I block such illegal login attempts? Does it help to change the default ports on the NVR? If so, then which ones? Any other ideas on how to block 'em from accessing my NVR? Could I block some specific ports in the TP Link router firewall? It is getting really annoying that some mom's hacker is just scanning the network for NVR's to attempt to access. Any other ideas on securing the network are very warmly welcomed.
Thanks!
Alex

